A2Cyber.com believes that any organization, large, small or miniscule, is susceptible to Cyber Security Threats as long as it is exposed to a networked environment or internet.
What is a Vulnerability Assessment?
A vulnerability assessment is the process of identifying, quantifying, and prioritizing the vulnerabilities In a system. Examples of systems for which vulnerability assessments are performed include, but are not limited to, information technology systems, energy supply systems, water supply systems, transportation systems, and communication systems.
What is Penetration Testing?
A penetration test, also known as a pen test, is an authorized simulated attack on a computer system, performed to evaluate the security of the system. The test is performed to Identify both weaknesses (also referred to as vulnerabilities). including the potential for unauthorized parties to gain access to the system’s features and data.
What is the difference between a Vulnerability Assessment and Penetration Test?
Penetration testing is Intrusive, and is a real attack simulation using specialized tools. Vulnerability assessment is non intrusive and does not exploit any weaknesses.
BENEFITS OF VULNERABIITY ASSESSMENT
- Identify known security exposures before attackers find them.
- Create an inventory of devices on the network & what level of risk the devices pose.
- Results help with the planning of upgrades and future assessments.
- Results help define the level of risk that exists on the network.
- Results highlight a business risk exposure
- A better understanding of the impact to an organization of such risk.
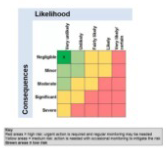
FREQUENCY OF VULNERABILITY ASSESSMENTS
To be effective, organizations must schedule Vulnerability Assessments periodically, such as monthly, quarterly or semi-annually and when there is a major update to a Network environment. Twice a year for Penetration Tests, if possible.
BENEFITS OF PENETRATION TESTING
- Helps to answer the question of How Secure your Network is?
- Helps you to prevent Information & Financial Loss
- Businesses can better secure their Information Systems and Infrastructure
- Penetration testing assessments are also useful in validating the efficacy of defensive mechanisms and determining how well end-users adhere to security policies.
Here are the Open Web Application Security Project's
Top 10 Vulnerabilities for 2017
OWASP TOP 10
- A1:2017 – Injection
- A2:2017 – Broken Authentication
- A3:2017 – Sensitiva Data Exposure
- A4:2017 – XML External Entities (XXE)
- A5:2017 – Broken Access Control
- A6:2017 – Security Misconfiguration
- A7:2017 – Cross-Site Scripting (XSS)
- A8:2017 – Insecure Deserialization
- A9:2017 – Using Component with Known Vulnerabilites
- A10:2017 – Insufficient Logging & Monitoring
A2Cyber.com can defend your business by Identifying your vulnerabilities & configuration issues & assist in mitigating and responding before cyber criminals can identify and exploit them. Such vulnerabilities when exploited by criminals can cost businesses & organizations hundreds of millions of dollars in downtime, lost revenue, stolen digital assets, compromised data, or stolen emails as discovered not long ago.

Secure your business. Safeguard your Organization.
The business environment is constantly changing and new threats and vulnerabilities emerge every day. A2Cyber.com’s Vulnerability Assessment Team assists in preventing network attacks by identifying the vulnerabilities and configuration issues that hackers use to penetrate your network. Our advanced scanning software detects live risks to businesses infrastructures by identifying new vulnerabilities and preventing unauthorized access.
A2Cyber.com can identify real risks to an organization’s data and infrastructure through testing against the world’s largest, fully tested and integrated public database of exploits.
The remediation plan provided by our cyber consultants gives organizations the tools necessary to make choices about which counter measures to employ, striking a balance between productivity, cost effectiveness and the value of IT assets being protected.
5 Steps to a great Vulnerability Assessment:
- Determine the hardware and software assets in an environment
- Determine the quantifiable value (criticality) of these assets
- Identify the security vulnerabilities impacting the organization
- Determine the threat levels or risk factor
- Enumerate Mitigation Steps from the highest risk to the lowest.
Adoption of industry standards, including a
Vulnerability Assessment and Penetration Testing, is a
vital step in minimizing these vulnerabilities.
Email : andy@a2cyber.com
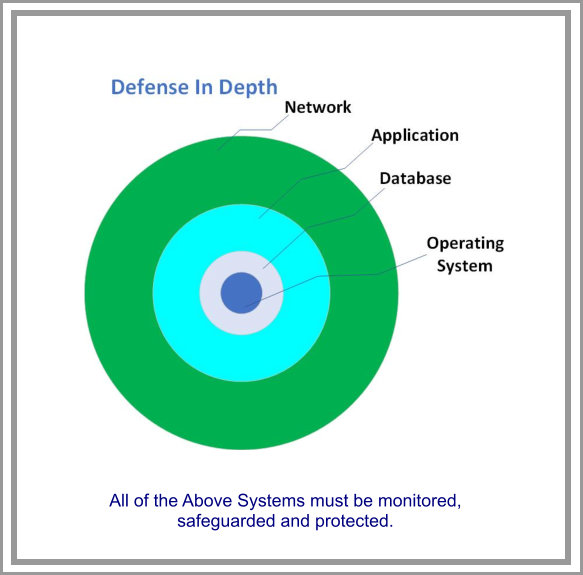
Some Of the tools we use